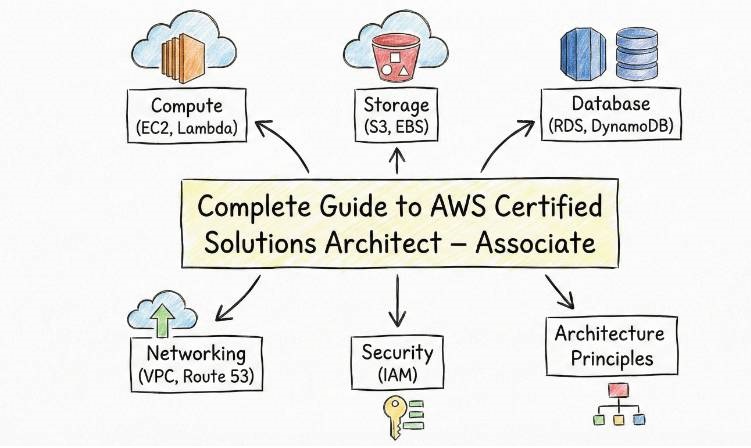
Cloud computing is no longer a “future” skill; it is the backbone of modern business. In my years of navigating the shifts from on-premise data centers to hybrid clouds and fully serverless architectures, I have seen many certifications come and go. However, the AWS Certified Solutions Architect – Associate (SAA-C03) remains the gold standard for anyone serious about building scalable, secure, and cost-effective systems.
What is the AWS Certified Solutions Architect – Associate?
The AWS Certified Solutions Architect – Associate is a certification that validates your ability to design and deploy well-architected solutions on AWS. It focuses on the AWS Well-Architected Framework, ensuring you can balance cost, performance, and reliability.
Who Should Take It?
- Software Engineers looking to understand the infrastructure their code runs on.
- Systems Administrators transitioning to Cloud Engineer roles.
- Project Managers who need to speak the same language as their technical teams.
- Freshers with a solid grasp of networking and computing basics.
Skills You’ll Gain
- Design Resilient Architectures: Learn how to use Multi-AZ deployments and Auto Scaling.
- High-Performance Computing: Selecting the right EC2 instances, storage (EBS vs. S3), and databases.
- Security & Compliance: Mastering IAM, VPC security groups, and encryption at rest/transit.
- Cost Optimization: Identifying ways to reduce monthly AWS bills using Spot Instances and S3 Lifecycle policies.
Real-World Projects You Can Do After
- Static Website Hosting: Deploying a global website using S3, CloudFront, and Route 53.
- Scalable Web App: Building a three-tier architecture with an Application Load Balancer and RDS.
- Disaster Recovery: Setting up cross-region replication to ensure data safety.
- Serverless APIs: Creating a backend using Lambda and API Gateway.
Preparation Plan
Depending on your current workload and familiarity with AWS, here are three paths to success:
7–14 Days (The Fast Track)
- Target: People already using AWS daily.
- Plan: Focus 100% on the exam blueprint. Take three full-length practice exams. Review every wrong answer and read the official FAQs for those services.
30 Days (The Standard Path)
- Target: Working professionals with some cloud exposure.
- Plan: Spend 1 hour a day on video courses and 2 hours on weekends for hands-on labs. Focus on VPCs, IAM, and S3 in the first two weeks. Spend the final two weeks on databases and practice tests.
60 Days (The Deep Dive)
- Target: Beginners or those moving from a different field.
- Plan: Take it slow. Spend 4 weeks purely on hands-on labs. Build, break, and fix things in the AWS Free Tier. Spend the remaining 4 weeks on theoretical concepts and exam prep.
Common Mistakes
- Ignoring Networking: Many fail because they don’t understand how VPC subnets and routing work.
- Memorizing Answers: AWS changes questions frequently. Understand the why, not just the what.
- Underestimating S3: It’s a simple service but has complex features (Storage classes, IAM policies) that are heavily tested.
Best Next Certification
After this, the AWS Certified Solutions Architect – Professional is the natural progression for those wanting to reach the peak of cloud architecture.
AWS Certification Overview Table
| Track | Level | Who it’s for | Prerequisites | Skills Covered | Recommended Order |
|---|---|---|---|---|---|
| Architect | Associate | Engineers & Architects | Basic Cloud Knowledge | Design, Security, Cost | 2nd (After Cloud Practitioner) |
| Developer | Associate | Software Developers | Coding Knowledge | CI/CD, SDKs, Serverless | 2nd or 3rd |
| Operations | Associate | SysAdmins / SREs | Linux/Networking | Monitoring, Deployment | 2nd or 3rd |
| Architect | Professional | Senior Architects | 2+ Years AWS Exp. | Complex Org Designs | 4th |
| DevOps | Professional | DevOps/SRE | Developer/SysOps Assoc | Automation, HA | 4th |
Choose Your Path: 6 Specialized Learning Journeys
Architecture is the foundation, but your career path determines how you use it.
- DevOps Path:
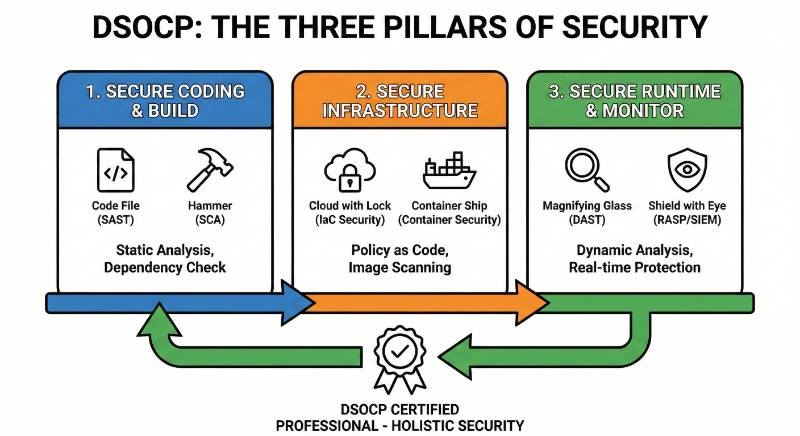
Focus on AWS CodePipeline, CloudFormation, and Elastic Beanstalk. This is about moving code from a laptop to production without human intervention. - DevSecOps Path:
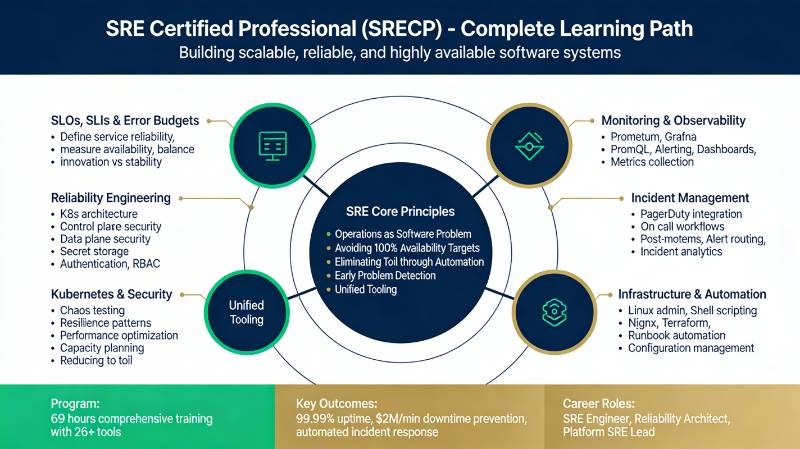
Prioritize AWS WAF, Shield, GuardDuty, and IAM. Security must be “shifted left” into the development process. - SRE Path:
Focus on CloudWatch, X-Ray, and AWS Health Dashboard. Your goal is reliability, latency reduction, and high availability. - AIOps/MLOps Path:
Dive into SageMaker and AWS Glue. This path is for those automating operations using machine learning models. - DataOps Path:
Master Redshift, EMR, and Kinesis. You are building the pipelines that feed the world’s data-hungry applications. - FinOps Path:
Use Cost Explorer, AWS Budgets, and Savings Plans. You help the company maximize every dollar spent on the cloud.
Role → Recommended Certifications Mapping
- DevOps Engineer: Solutions Architect (Assoc) → DevOps Engineer (Prof).
- SRE: Solutions Architect (Assoc) → SysOps Administrator (Assoc).
- Platform Engineer: Solutions Architect (Assoc) → Advanced Networking (Specialty).
- Cloud Engineer: Cloud Practitioner → Solutions Architect (Assoc).
- Security Engineer: Solutions Architect (Assoc) → Security (Specialty).
- Data Engineer: Solutions Architect (Assoc) → Data Engineer (Assoc).
- FinOps Practitioner: Cloud Practitioner → Solutions Architect (Assoc).
- Engineering Manager: Solutions Architect (Assoc).
Next Certifications to Take
Once you have earned your Associate badge, you shouldn’t stop. Here are three directions you can go:
- Same Track (Vertical): AWS Certified Solutions Architect – Professional. This proves you can handle complex, multi-account enterprise environments.
- Cross-Track (Horizontal): AWS Certified Developer – Associate. This is excellent for understanding how to write code that specifically leverages AWS services like DynamoDB and SQS.
- Leadership/Management: AWS Certified Cloud Practitioner (if not already taken) or looking into specialized ITIL/Project Management certifications to lead cloud transformation teams.
Where to Get Help: Top Institutions
If you are looking for guided training and certification support, these organizations provide excellent resources and mentorship:
- DevOpsSchool:
A premier destination for community-led learning. They offer deep-dive sessions that go beyond the exam, focusing on real-world application and job readiness in the DevOps space. - Cotocus:
Known for their hands-on approach, Cotocus provides specialized training environments where you can practice real-world scenarios under the guidance of industry veterans. - Scmgalaxy:
A massive hub for SCM and DevOps resources. They offer a wealth of tutorials, community support, and certification guidance for engineers looking to level up. - BestDevOps:
They specialize in curated content for modern engineering roles, focusing on the latest tools and practices required to pass AWS exams and excel in a career. - Specialized Schools: For niche topics, you can explore devsecopsschool.com, sreschool.com, aiopsschool.com, dataopsschool.com, and finopsschool.com for role-specific training.
Master FAQs on AWS Certified Solutions Architect – Associate
1. How difficult is the exam?
It is moderately difficult. It requires a mix of theoretical knowledge and the ability to solve “scenario-based” questions. It’s not about definitions; it’s about choosing the best solution for a specific problem.
2. Do I need to know how to code?
Not for the Solutions Architect – Associate exam. You should understand the concepts of applications and databases, but you won’t be asked to write Python or Java code.
3. How long is the certification valid?
It is valid for 3 years. After that, you can recertify by taking the current exam again or passing the Professional level exam.
4. Is there a prerequisite?
No. While many start with the Cloud Practitioner, you are allowed to jump straight into the Solutions Architect – Associate.
5. How much does it cost?
The exam fee is $150 USD. If you have passed an AWS exam before, you usually get a 50% discount voucher for your next one.
6. What is the passing score?
The passing score is 720 out of 1000. The exam uses a scaled scoring model.
7. Can I take the exam from home?
Yes, AWS offers online proctored exams via Pearson VUE, or you can take it at a physical testing center.
8. Is this certification enough to get a job?
It is a door-opener. It proves you have the knowledge, but you will still need to demonstrate your skills through interviews and practical experience.
9. Which is better: Developer or Solutions Architect?
Solutions Architect is more broad and generally more valued for career growth in engineering and management. Developer is better if you are 100% focused on writing code.
10. How many questions are on the exam?
There are usually 65 questions, including multiple-choice and multiple-response.
11. What if I fail?
You must wait 14 days before you can retake the exam. There is no limit on the number of attempts, but you must pay the full fee each time.
12. Does it cover Multi-Cloud?
No, this exam is strictly focused on Amazon Web Services (AWS) infrastructure and services.
General FAQs
1. Is the AWS Solutions Architect – Associate exam difficult in 2026?
It is considered a “Moderate” difficulty exam. It has shifted away from simple memorization to scenario-based questions. You will be presented with a business problem and asked to choose the best architecture based on specific constraints like cost or performance.
2. How much does the certification exam cost?
The standard registration fee is $150 USD. In India, this typically translates to approximately ₹11,000 – ₹12,000 (plus applicable taxes). Note that after passing any AWS exam, you receive a 50% discount voucher for your next one.
3. What are the official prerequisites for the exam?
Technically, there are no mandatory prerequisites; you can take it without having any prior certifications. However, AWS recommends having at least one year of hands-on experience in cloud design and a solid understanding of networking and security.
4. How long does the certification remain valid?
The certification is valid for 3 years. To maintain your status, you must recertify by either taking the current version of the same exam or by passing the higher-level AWS Certified Solutions Architect – Professional exam.
5. What is the retake policy if I do not pass?
If you fail the exam, you must wait 14 calendar days before you are eligible to retake it. You must pay the full exam fee for every attempt. There is no limit to the number of times you can attempt the exam.
6. Does the exam require coding experience?
No, coding is not a requirement for this specific certification. While you should be comfortable with technical concepts and the AWS Management Console, you will not be asked to write or debug code during the test.
7. Can I take the exam online from my home?
Yes. You have the option to take the exam at a physical testing center (Pearson VUE) or via an online proctored environment from your home or office, provided you meet the system and room requirements.
8. What is the average salary for an AWS Certified Solutions Architect in India?
In the current market, mid-level professionals with this certification typically see salaries ranging from ₹8 LPA to ₹15 LPA. For senior roles or those who pair this with Professional or Specialty certifications, the packages can extend significantly higher, often reaching ₹25 LPA to ₹40 LPA.
Conclusion
In my years of watching the industry evolve, I’ve seen that the most successful engineers are not those who simply “know” the tools, but those who understand the architectural “why” behind them. The AWS Certified Solutions Architect – Associate is more than just a badge on your profile; it is a declaration that you can look at a business problem and design a solution that is secure, resilient, and cost-effective.
For managers, this certification provides the vocabulary to lead high-performing teams. For engineers, it is the key to moving from execution to strategy. As we continue to build in a world that is increasingly cloud-native, this knowledge is your most valuable asset. The journey might seem long, but with a structured plan and the right mentorship, the transition is entirely within your reach.